Introduction 500 words
As per the previous discussion, a well-known organisation “Walkgrove” wants to implement an Information Security Management System. It is an important element that helps different organisations using technology and the internet in acquiring a code of conduct which is responsible for providing guidance, security and best practices which can be utilised to enforce but throughout the world. It has been functioning with many large organisations since it was founded in 1994 (GHolami and Murugesan, 2011). It provides education in many ways, such as through the internet, coaching, and traditional classroom training. It even uses workbook design to ensure that the clients are satisfied in the best possible manner.
Even though the company has been quite efficient in its functionality in the past, it is now expected to face risk problems moving forward. This is mainly because most of the functionality performed by this company is through the internet and technology, which includes the channels that provide learning, payment methods and even its records. This poses a serious threat to Walkgrove because cybercrimes are more rampant in 2022, and the rate of these crimes is increasing daily (Marchewka, 2016). According to research, in 2023, cybercrimes are expected to reach the highest and will incur massive losses to many businesses throughout the Globe.
Walkgrove is expected to be one of those businesses because it does not have a proper Information Security Management System and desperately needs one.
Usage of Project Management System
The only way that Walkgrove can implement a proper Information Security Management system is by utilising a systematic project management system. The suggested method in this scenario is the ‘Waterfall methodology”, which is considered one of the Sequential Development procedures in that it flows just like a waterfall in the implementation of a project; it is inclusive of various steps such as Analysis, Designing, Implementation, Verification, Development and maintenance phase. With this approach, the company Walkgrove can map out the project of implementing the Information Security Management System into distinctive and sequential phases (Schwalbe, 2015). Additionally, this method is highly effective and efficient as it ensures a systematic
structure for implementing ISMS in Walkgrove. The next step will only initiate if the previous one is completed.
Rationale
The main reason why this research is so important is that most successful and running businesses utilise the conceptuality of technology and innovation in their everyday workings. The latest innovations of technology are continuously being introduced, and so are the risks of them being hacked (Stewart, 2010). With the utilisation of this research, organisations that are adopting the latest version of technology or Information Security Management system will easily follow a proper systematic channel; they will also be aware of the risks of implementing such projects.
Problem Statement
The project under consideration is the implementation of an Information Security Management System in Walkgrove. The present situation of Walkgrove is that it does not have any proper system that can protect it from cyber security threats and provide proper guidance and practices, which means that the organisation is expected to deplete in the future. This project will help Walkgrove implement an Information Security Management System, ensuring that the organisation stays operational, efficient and protected (Meredith et al., 2017). The gap between the future and present state is the various risks that come with the implementation of a project, time and effective planning.
Research Questions
- Why should the organisation implement Information Security Management System?
- What are the expected challenges while implementing a project?
- What is the systematic approach to implementing the whole project?
- What are the expected costs and time duration required to implement this project?
- What can be done to maintain the quality of work delivered?
- What are the risks associated with handling and implementing the whole project? And how can they be mitigated?
Research Methods (20 percentage weightage) 8500×0.2= 1700 words
Data Collection Data (700 words)
The conceptuality of data collection is considered a vital element of any research; the data collection procedure involves collecting information from different sources to come up with a solution to a particular issue. This procedure is also responsible for the evaluation of the outcomes and making predictions of different trends and possibilities in the future (Johhson and Sylvia, 2018). To collect the data, it is essential to collect the most basic data related to the provided situation and then progress with the other type of data. There are two types of data collection methods, the first one is known primary data and the second one is known secondary data. For the provided research, qualitative research was conducted on secondary data (Harris, 2001).
Secondary data is also known as desk research mainly because it is a research method involving the usage of data already existing. The data is then summarised and collated to ensure an increment in the overall efficiency of the research being conducted (Vartanian, 2010). This data is inclusive of various research materials that have been published in the form of research reports or any other similar documentation. The secondary data is readily available in different public libraries, educational institutions, etc. The main reason for considering secondary research is because it is one of the most cost-effective and time-efficient data collection methods. Following are the ways that the secondary data is acquired for this research (Harris, 2001).
Data from the internet is one of the most popular ways to gather secondary data. The data on the internet is readily available and can be obtained with a single click of a button. This particular type of most of the data is acquired practically free from all sorts of costs; in some situations, only a negligible amount was required to download the already available data. These websites contained lots of valuable information well suited to this research’s project management needs. However, it was made sure that the data was only gathered from the websites and internet sources that were the most authentic and trustworthy ones (Johhson and Sylvia, 2018).
The Public Libraries were another good source utilised to gather secondary data for this research. All Public libraries have copies of relevant research conducted previously by different researchers or authors. This source is considered a storehouse of important information and documentation from where all the relevant information can be extracted. During the data collection process, it was found that most public libraries had a large collection of government- related publications that included market-based statistics and a huge collection of business- related data, which was very useful for this particular research (Vartanian, 2010).
This type of secondary data collection source is mostly overlooked in terms of its importance and the quality of data it can provide; this is mainly because these educational institutions, such as colleges and universities, which were considered in this research, conduct more research than any other organisation (Tripathy, 2013). The data which these universities acquired was mostly for primary research. However, these colleges and universities were approached for this research, and all the relevant data was requested.
Commercial Information Sources
This includes all the local newspapers, television shows, magazines, and radio, which were also great source of secondary data and was very beneficial for this research (Harris, 2001). With the utilisation of these commercial sources, all the firsthand information was acquired, which was related to the incorporation of various ideas with the utilisation of project management tactics that were considered by different businesses. Apart from this vital data, they also gave an insight into various economic developments, market research, demographics and political agenda that supported this research (Vartanian, 2010).
Government and Non-government Agencies
The secondary data were also acquired from different governmental and non-governmental agencies. However, there was little cost to download or utilise the data provided by these agencies. The data was gathered from these agencies mainly because of its reliability, trustworthiness and authenticity (Tripathy, 2013).
Data Analysis (1000 Words)
The conceptuality of data analysis refers to a procedure responsible for inspecting, transforming, and cleaning data to discover information that will be useful for the given research (Joffe, 2012). Additionally, with data analysis, informed conclusions can be drawn alongside supportive decision-making. There are various approaches or facets of conducting data analysis that is inclusive of different techniques, names, and domains. In today’s world, the conceptuality of data analysis plays a very important role in the whole decision-making procedure and helps different firms operate more effectively. The data analysis approach considered in this research is known as Thematic Analysis.
Thematic Analysis is a very good approach in data analysis if there is qualitative research used on secondary data, which was done in this research (Braun and Clarke, 2012). The thematic research directly considered the research questions, collected data from all the relevant sources, and analysed them. The utilisation of thematic analysis allowed flexibility in the interpretation of the data and also allowed approaching a large sum of data collected from various secondary sources more easily by sorting them out into different and broader themes.
In the whole research, Deductive reasoning was utilised, which is a logical approach that will assist massively to progress from general ideas to specific conclusions. In most scenarios, it is contrasted with inclusive, starting with specific observation and then forming generalised conclusions after understanding that the thematic analysis is well suited to this research and the right approach was decided. The part included following a sex step format which is given below (Joffe, 2012).
The first step in the thematic analysis is known as Familiarization, in which the data is properly understood; this is mainly because it is very critical to get a thorough overview of all the data that was collected in the data collection part before the actual analysis of individual terms and items that were involved. This included a transcription of all the audio and videos obtained from the commercial sources, reading through all the texts acquired from different secondary sources, making all the initial notes and then going through the data to ensure familiarity.
After the data was properly familiarised, the next step involved coding the collected data. Coding involves highlighting an important part of the text, mainly in the form of different sentences or phases. When the important data was highlighted from the important text, shorthand labels or codes were assigned to them to describe their content (Braun and Clarke, 2012). During this stage, it was made sure that everything was thorough, where all data was gone through, and all the important or relevant elements were highlighted. In addition to highlighting all the relevant content, it was made sure that each of them had its codes, and new codes were added as the data was gone through.
After going through the whole data, all the data was collated into different groups identified by the codes. These codes helped gain a condensed overview of the common meaning or the main points reoccurring in the whole data.
After the codes, the codes were created and the patterns among them were identified, the next step had to do with assigning the themes. These themes are broader than codes; many codes will be compiled to form a single theme. During this stage, some codes acquired that were too vague or irrelevant for this research were discarded (Clarke, Braun and Hayfield, 2015). However, some codes became themes in their rights. It was ensured during this stage that the themes being created informed something useful about the data for this research.
After making sure that the themes were valuable and provided an accurate representation of the data, the data set was considered again and compared with different themes to see if anything was missing. It was also checked if these themes were present in the data, and if necessary, amendments were made to improve these themes (Guest et al., 2011). There were some situations in which problems were encountered related to the themes. Different tactics were used to cater to such a dilemma, such as splitting the themes up, combining them, discarding them, or simply creating new ones. The tactics were decided based on whatever makes the themes more accurate or useful.
Step 5: Defining and Naming Themes
After the final list of themes was acquired, the next step involved naming and defining all of them. Defining the themes involved understanding what each of the themes meant and then how these themes can aid in understanding the secondary data collected (Neuendorf, 2018). During this step, it was made sure that all of the themes had a succinct and easy name which was easy to understand.
In the last part of the analysis, like all the academic content, a proper introduction was provided to establish the suggested research questions, aims and the selected approach. It also includes other important sections such as the Research methods, critical analysis and self-reflection related to how this research helped in the development of the researcher (Joffe, 2012).
Findings and Discussion (8500×0.5=4250)
Reasons to Consider Project management
The conceptuality of Project management within an organisation is a critical conceptuality that can not be overstated. When this conceptuality is properly utilized, then it allows the firm’s procedures to run more smoothly and swiftly. Additionally, it allows the time included in the whole conceptuality to lay their focus on the working procedures that actually matter, that are free from all sorts of distractions which are mostly caused by being off track or not having efficient systems to control the budgets. Project management allows the organisations or businesses in delivering results that have a direct impact on their bottom line, while enabling the workforce of the organisation to see how their working procedures contribute to the strategic goals of the organisation. Following are some of the reasons why the conceptuality of project management should be considered in the working functions of an organisation. Having a proper planning structure in place allows the organisation to deliver the work on time and within the allocated budget. With the utilization of project management methodologies, the organisation or business can easily map their whole journey right from the outset, allocate deadlines and budgets. This allows the organisation to be more effective when it comes to allocation of the budget, which ultimately helps in avoiding delays and overspending on a simple project
Most of the organisations have a diverse workforce working for them which makes the concept of working together extremely hard. However, with the utilization of project management procedure, the organisation can have a massive reduction when it comes to complexity in collaboration and in return also has a massive increment in the level of transparency and ensuring accountability, even in situation when the employees are working across various departments or teams. When the organisation or business is well aware of the direction where the project is headed, then it allows the firm to get a much deeper understanding on where its resources are being utilized, what it needs to prioritise and at what time. The project management also makes sure that the whole conceptuality stays on track and makes forecast regarding the issues it is expected to face and make timely decisions before they can become problems for the organisation. The organisations can also do away with bottlenecks and make smarter data driver decisions with the utilization of Project management. Having such a conceptuality allows the firms to scale high performance and build on their team best practices with the utilization of data and learning which was acquired from previous projects. Project management enables the organisation to pinpoint the areas where the whole team is excelling and where it needs to improve on. When the organisation measure its key performance indicators then it can easily create and track personalized benchmarks which would enable it to understand how the team is performing through the whole project.
In today’s world more and more of the organisation’s daily work is becoming project-based which means that more and more employees are now finding themselves being involved with managing projects of their organisation, despite not being traditional project managers which suggests the fact that the importance of project management is growing at a very fast pace. For the organisations such as Walkgrove which is considering a transition towards the implementation of Information Management system the conceptuality of Change management will be of utmost importance as it will help the company go through the transition much more effectively.
Understanding the Role of Change Management
Change management is considered as an important part of Project management which is inclusive of a systematic approach which is used to deal with different transformations or transitions related to the goals, procedures and technologies of an organisation. In the provided scenario where the company Walkgrove wants to implement an Information Security Management System is also a transformation or a transition which is well suited to this conceptuality. The phenomenon of change management is extremely complex with it comes to different situations such as Merger, Acquisitions or incorporating something in the working function. The technical side of this conceptuality which is inclusive of different financial agreements associated with the deal, integration of additional or new business systems, making decisions about the new structure of the business etc. However, getting people on board and making them participate after the whole transition has occurred will be a key difference whether the organisation will be successful or a complete failure. This is mainly because after the whole transition, people working in the organisation such as Walkgrove will have to perform their jobs or roles much differently and adapt to new procedures such as Information Management systems which would have a significant impact on the initiatives taken, this is the main reason why the softer side of the transition can also be the complex and harder side of it. However, companies like Walkgrove can consider the conceptuality of structured approach which help it to manage the workforce and employee side of its functionality, which will ultimately make a huge impact when it comes to organizational success. It makes a huge positive impact on the people side of change by creating a new organisation after transformation, designing new working procedures and implementation of new technologies which would allow the employees to see their full potential, this is mainly because the whole financial or monetary success depends on how well the workforce of the organisation embrace the change. Change management involves application of well structured procedures and setting of tools which will aid in leading the workforce to achieve the desired result. The prime focus of change management in this side is to help the employees in engaging, adopting and using the change in their everyday working functions. The element of change management is both a procedure which can help Walkgrove in adopting Information Security Management system and a competency which can help the company to stay on top of its competitors.
Change Management as a Procedure
The change management as a procedure is responsible for enabling the practitioners within the working environment of an organisation to leverage and scale all the change management procedures or activities that have impacted the people part of the organisation during the whole transition. The Prosci methodology provides three steps which makes the whole concept quite distinctive and systematic which is provided in figure 1.
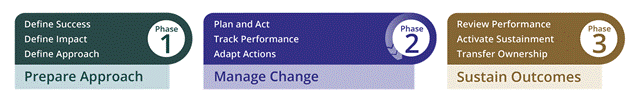
Figure 1: Prosci Three Phase Process
During the first phase the organisation such as Walkgrove will be deciding what it wants to achieve, how the employees involved in the working functions would have to perform their jobs different and requirements in achieving the success. In the second stage which has to do with managing change, the company such as Walkgrove will be preparing, supporting and engaging people and ensuring if it is doing the right job or if any amendments are needed with the working function. In the last step of the change management as a procedure, Walkgrove will be making sure if it is done with the whole changing and the current position it is at after the change. In the last step, it will also be making sure that the whole change sticks and transfer of ownership.
Change Management as a competency
The conceptuality of change management is considered as a leadership competency which is responsible for enabling change within an organisation. The strategic capabilities which the concept of change management includes are designed to have an increment in the responsiveness of the organisation and its change capacity. Change management as a competency is inclusive of being able to lead the whole transition for the organisation, by being an active sponsor of change and showcasing commitment towards the transition both at an individual or organizational level.
Reasons to consider Change Management
There are many reasons why an organisation such as Walkgrove should consider the conceptuality of Change management. However, the three main reasons of considering Change management includes change happening one person at a time, ignoring the people side of change being extremely costly and increment in the likelihood of success. It is very easy to consider the change at an organizational level such as the company Walkgrove incorporating Information Security Management System which included different financial structuring, data integration of systems and some other physical changes. However, the organizational change starts happening one person at a time regardless of the kind of change being considered, this mainly because business-wide change only happens when all of the employees starts performing their duties differently. It is quite evident that people change, whereas the organisations remain the same. The cumulative effect of successful individual change leads to successful organizational change. Despite making the change, if the employees of the company do not change their everyday working functions then the whole transition will be useless. If Walkgrove completely neglect the people side of the change, then it can have a massive impact on its gains such as decline in the level of productivity, managers showing unwillingness to contribute towards the change, stakeholders neglecting meetings, stress, frustration, fatigue and so on. The projects such as that of Walkgrove will also suffer if it misses deadlines, budget overruns, and reworking on the same task. Such consequences will have massive negative impacts on the health of project and the organisation itself. However, these goals can easily be mitigated by companies like Walkgrove if it deploys a well-structured approach towards all sides of change. The growing body of data suggests the effect that a proper change management system has on reaching the objectives of the whole project. As per the research conducted by Prosci shows that 93 per cent of organisations that have effective change management were able to either achieve the objectives or exceed them, in comparison to the 15 per cent of the organisations that had poor change management in place.
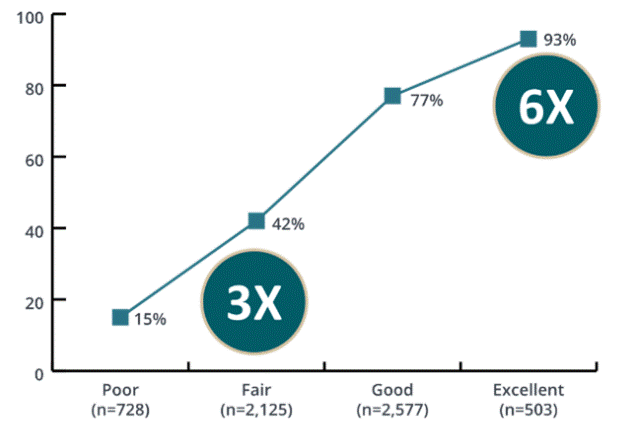
Figure 2: Correlation of Change Management Reaching Project Objective
In simple terms, if the organisation such as Walkgrove has excellent change management system then it is six times more likely to meet the objectives of the plan such as the successful implementation of Information Security Management Sytems than those having poor change management systems in place. The same research also showcased that if the organisation has a poor change management system in place, it is still likely to be successful in change than applying nothing at all.
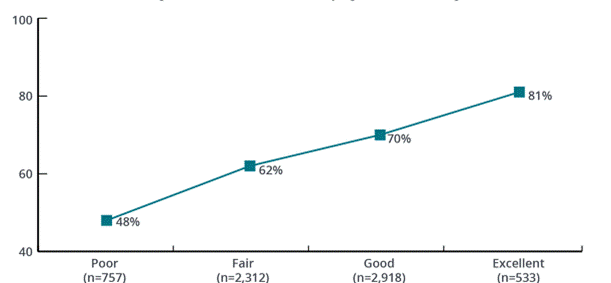
Figure 3: Percentage of Organisation Staying On or Under Budget
Successful Implementation of a Project
The usage of change management models is mostly overlooked, which is mainly because the organisation are in a rush to implement the changes. This is one of the most critical error which should be avoided by the organisations that are undergoing transformation such as Walkgrove. Furthermore, incorporating an effective change model system will strengthen the whole change procedure. The whole history is filled with different people who failed in their attempt to reach a certain goal and ended up paying an ultimate price for it. An example can be taken of hard to reach destinations such as the North Pole, South Pole, Mouth Everest, Northwest Passage and so on. The people that embarked on the journey to reach these destination did not fail because were not brave, rather they failed because they did not come fully prepared to embark on such a journey which may be inclusive of lack of practice, or the necessary equipment which were vital for the survival there. While most of the people failed to reach that destination because they were not properly prepared however, some of them failed because they made irresponsible decisions as they believed that they have the capability of doing everything and were full of bravado.
However, the failures of these travelers provided valuable intel so that the following travelers would not repeat the same mistakes. In such a situation, to achieve success a person or an organisation should know what to avoid and the things to do different to better achieve success. These Change management models act as a map for the organisations that are undergoing some sort of transition such as Walkgrove in its quest to implement Information Security Management System. These maps were created solely for providing directions and instruction to ensure that the whole transition or transformation happens successfully and without any complications. According to most researchers, when the conceptuality of Change management is neglected when going through a certain transition is just like going to the South pole on a Hot Air Balloon which is simply not possible. The change management models will allow Walkgrove to forecast the whole procedure of change and make the people prepare for it. Additionally, it is well known that the procedure of change should not begin without known the end result and the means through which it will be measured. With the utilization of Change management models the company such as Walkgrove will set up relevant objectives, create schedules and allocate budgets, which is a good way to measure how the change is being managed and all the useful interventions. Apart from the measured outcome, having a change model also gives accountability to everyone involved in the whole procedure of change according to their roles.
This is mainly done by describing and simplifying the change procedure in a way which is easily understandable for everyone working in Walkgrove that is considering the change. Change models also helps the organisation in the identification of potential areas of resistance and design strategies to help with the reduction of that resistance before the whole procedure of change begins alongside giving the whole organisation the confidence to proceed with the whole project. Following a proper and systematic change management model ensures that the investment which was made in the whole transition or the project are not wasted and the element of budget is properly maintained. These investments are not only the financial aspect of the organisation but it also includes people, where the change management model also makes sure that the workforce and their contributions are well maintained. There are various change models such as Kurt Lewin, ADKAR, MckKinsey’s 7-S model and so on which can be utilized by Walkgrove in successful implementation of Information Security Management system. The organisations that consider the change model in their transition are 87 per cent more likely to have a successful implementation than the organisations that neglects it. Another research as provided in Figure 4 suggests that having a well suited, and effective change model will increment the likelihood of success by 73 per cent
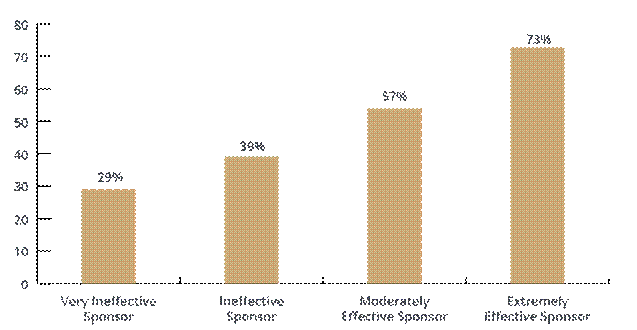
Figure 4: Contributions of Effective Change Models
The Project Risk Management Procedure
Understanding Risk Management
It is quite evident that as the time progresses the projects are becoming dynamic, which makes it very important for the organisations to have the ability to manage risks or uncertainties that comes with such transitions. The increment in the demand for skilled project management professionals are truly reflection of this trend where it estimated that 23 million jobs related to project management will be added in all industry by the end of 2027. In the area of project management, the terminology of risk management is associate with practice that involves identification, evaluation and prevention or mitigation of a risk related to the project that has the ability to impact the desired output. It is the ultimate responsibility of the project managers to perform the functionality of the risk management process throughout the timeline of the whole transformation or transition of the project. To manage or deal with all of the risks effectively that Walkgrove is expected to face in implementing Information Security Management System, it is essential that the project managers involved in this scenario should have a clear understanding associated with the project, which will help with the identification of all the possible barriers that could have an impact of the team’s ability to produce the desired results.
Types of Risk
Apart from understanding what does the risk management means, it is also essential for the project managers to know what type of risks they are expected to face, these risks are mainly dependent the type of project being considered. There are several risks that occur very frequently when dealing with a certain project regardless of kind of project being considered. For the company like Walkgrove that is implementing the Information Security Management System, some of the risks it is expected to face are the Cost, Schedule, and Performance. The cost is inclusive of all those risk events that have a direct impact on the budget of the project, especially the ones that will result in completion of the project by going over the intended budget limit. There are also various errors or risk included in the cost estimation procedures which are in addition to the external factors. The scheduling risk is inclusive of all the unplanned events that causes the projects to be halted or delayed. The major reason why Walkgrove is expected to encounter this risk is solely because of Scope Creep which is one of the common reason for scheduling issues and delays of the projects. The last issue which the company is expected to face is related to the performance which is inclusive of all those events or situations that produces inconsistent results related to the specifications of the project.
Steps included in Risk Management
To make sure that the whole project is well protected from all of the planned and unplanned risk, it is essential for the project managers of the Walkgrove to follow a proper and systematic risk management procedure which will help the identification, understanding and responding to all the threats or opportunities. Before the procedure begins, it is very important to get a full grip of the practices and risk work for the project under consideration. Following are the steps which Walkgrove is expected to consider while undergoing the risk management process. The first step in the risk management process has to do with the identification of the potential risk which is expected to impact the whole project of implementing Information Security Management System. The next step is to assign the ownership of different risks which were identified to the team members that will have the responsibility of overlooking that opportunity or threats. In most of the scenarios the project managers assign the ownership of overlooking after all the risks have gone through proper analysis and have been prioritized, however if Walkgrove takes this step early then it will be extremely beneficial. The third step is directly associated with the analysis of each of the risk involved, which helps with the understanding of the driving factors and all of their potential effects. In this step, it is essential for the project managers that are dealing with certain type of transformation such as Walkgrove to consider the breadth and depth of each of the threat at this stage, which will help in the evaluation related to the severity of each of the risk involved such as cost, scheduling and performance in the case of Walkgrove. After that, all the project issues will be prioritized based on their urgency and severity of impact that they could end up causing. After undergoing the prioritization process, the next step involves responding to the identified risks which should be in accordance with the selected risk management approach. There are two main types of risk management approaches, the first one involves prevention of the risk from happening and the second one involve mitigating the impact if it does end up occurring. This step will be responsible for taking the action and building a response to the provided scenario. In the last step, the project manager will be monitoring the whole process and making sure that nothing falls short.
Even though there are clear and systematic steps involved in the risk management process which can be utilized by Walkgrove in the implementation of Information Security Management System, this should still be an ongoing effort for the whole firm and the project managers involved. This is mainly because the risks are unpredictable by their inherent nature and the project managers need to have the agility and discipline to continuously face and mitigate the effects of these risks,.
Dealing with Challenges or Risks in Project Management
It is extremely impossible to completely eliminate the element of risk when dealing with a certain steps. However there are some additional steps which can be considered by the project managers of companies like Walkgrove to efficiently manage the projects allocated to them alongside having a reduction in the amounts of risk being faced.
Creation of Risk Management Plan
It is well enforced by all the researchers and everyone having experience in project management to have a strong project plan in place, which will allow the project managers to manage tough situations with ease. Additionally, there are also some ancillary plans which are mostly encompassed in the Project Plan, such as the Risk Management Plan. According to various research, it is quite evident that the risk management plan should be defining the methodology for identification and prioritization of the risk, alongside other crucial elements such as the risk tolerance which means that how the employees of the organisation such as Walkgrove will be responding to the risk and how well the risk was communicated in the first place to all the stakeholders. The formulation of such a plan takes lots of time and efforts, however making such investments in the planning or initial stages of the project pays off immensely by the creation of roadmap which has the responsibility of guiding the whole team throughout the whole execution phase.
Keeping Risk Register Up-to-Date
The element of risk register which can be inclusive of the risk management plan or be a separate documentation, is a lost of all those risks that have the ability of impacting the whole project which is currently under consideration. With the utilization of this documentation, allows the organisation to not only keep a track of the risks but also stay on top of the potential issues, therefore it is very essential for the organisations such as Walkgrove to keep this register up-to-date, so it always has an accurate information to refer to. With the utilization of Risk Register allows the organisation to keep a track of the risks or challenges that have already occurred, response of the team and birthing of new risks which were undetectable initially. If Walkgrove is able to keep its risk register up-to-date and makes sure it is incorporative of all the other planning elements then the whole team of the organisation alongside its stakeholders will be well aware of state of the project.
Understanding Risk Events
Thinking about the element of risk as possible outcome rather then a risk event itself is one of the common mistake in the department of Risk management. For instance, if the organisation Walkgrove “misses its deadline” and the people identify it as a risk then it is certainly wrong, this is mainly because missing the deadline is not a risk to the project but a threat. It is essential for the companies to understand the key difference here if they want to have a reduction in this department.
Being Proactive instead of Reactive
Most of the project managers make a common mistake when it comes to risk management, which is to consider a reactive approach in this department rather than being proactive. While it is necessary for the project manager to react when an uncertain event has occurrent but at the same time it is equally important that the project manager takes a step back and view the whole transformation through a proactive eye. With the investment in the initial sages of the risk management procedure and making complete analysis of each of the risk involved, it is quite evident that organisation such as Walkgrove can easily prepare itself to take preventative steps to have a reduction in the probability of risks from happening, rather than react when the damage has been already done. This allows the organisation to save lots of cost and time, in their working functions.
Developing Project Management Skills
Having a strong foundation in Project management skills is something that allows effective management of projects and the risks associated with them. Additionally apart from practicing it is also important to stay updated with the latest trend associated with the industry in which the organisation is functioning, such as for Walkgrove its is functioning in the digital learning industry. The project managers of this company should be actively involved in attending various conferences and workshops which is considered as one the finest way to refine the skills.
Conclusion, Limitations and Recommendations
Conclusion
In conclusion, it is quite fair to say that the project management scenario in which the company Walkgrove which is functioning in E-learning industry is now will to incorporate the functionality of Information Security Management system to ensure that it can sustain in the long-run. With the utilisation of such a concept it is quite evident that the company will be able deal with different cybercrimes and other hacking problems, right now the company is under serious threat of being hacked. Even though the above stated project might seem simple at the very first glance, however this is not the scenario since it is a project based on technological innovation therefore it needs to be implemented in a systematic and an efficient manner which will allow it to serve its purpose. There are certain elements which are required to be taken into consideration such as the challenges, and risk which Walkgrove is expected to face. The systematic manner of project management which can be utilised to incorpoate Information Security Management System in working functions of Walkgrove. As per the above provided discussion, to ensure that the whole project of Walkgrove gets incorporated in a systematic and right manner it has to consider the functionality of Project Management in its working functions which will set a pathway for the whole project. In addition to this the project management also allows the organisation or business to deliver the results which have a direct impact on the bottom line, alongside making sure that the whole team involved in the project works efficiently and effectively.
The additional benefits of using project management in the working functions include saving time, saving money, improvement in internal communication, making better decision, and iteration on company’s success. Reviewing the provided scenario, it is quite evident that Walkgrove is going through a transition or a transformation, which means that the conceptuality of Change management is of equal importance and will make sure that the whole transition falls through as per the expectations and the budget intended. To make sure that everything associated with the implementation part of the project is done in an effective and systematic manner, different change management models can be utilised by Walkgrove such as ADKAR, Kurt Lewin’s or Mckinsey’s change mode. Having such model in place allows the organisation such as Walkgrove that is undergoing a certain transition to have a map which is filled with directions and pathway to follow, and are made on the basis of failures that other organisations made. These models ensure that such mistakes are not repeated. With the utilisation of change management Walkgrove is expected to have six times the efficiency of a normal working function . The conceptuality of Risk management is of equal importance when it comes to the adoption of Information Security Management System in Walkgrove, which is mainly because Walkgrove is expected to face three main risks while adopting the projects which are associated with the costing, scheduling and performance. To ensure that the risk management process is in order, the company Walkgrove will have to consider six main steps which includes identification of the risks, assigning of the ownership, analysis of the risks, prioritizing the risks based on severity, responding to these risks and in the monitoring the risk management strategy. Furthermore, if the company Walkgrove does end up encountering a risk then it can consider five ways to reduce or mitigate it which includes creation of a risk management plan, keeping the risk register up-to-date, understanding of the risk event, being proactive instead or reactive and further developing management skills.
Limitations
The whole discussion associated with this research was based on secondary research and thus has some limitations. This is mainly because the secondary data is very easy to find but there are some drawbacks of using this data. This includes the secondary data being too vague or generalized which makes it very difficult for the companies or researchers to make a certain decision. The information associated with the data which is acquired from the secondary sources might not be accurate, which is why it is essential to check the source of the data from where the data is being acquired. The data which is being acquired might be old and is no longer relevant, or the sample size which has been considered in the secondary research might be too small. However, the usefulness of the secondary data might be limited due to two of the main reasons which are stated. The first one is related to relevance in which it quite evident that secondary data will provide all the answers which are needed, furthermore the objectives or the methodologies which are utilized in acquiring the data might be appropriate for the given circumstances. The second one is related to the lack of accuracy which might be based on the research design, sampling design, analysis point of view and so on. This research was also primarily based on qualitative data which means that it is very difficult to verify the results of the qualitative research since everything is over open ended and is not statistically representative.
Recommendations
Following are the recommendations which can be utilized by the company Walkgrove for the successful implementation of its project
Consideration of Work Breakdown Structures
The conceptuality of work breakdown structure will allow the organisation such as Walkgrove that is undergoing a transition to have a visual format which will help it in breaking down the whole project of Information Security management system into small deliverables which can be easily placed in the project schedule. Additionally with the usage of Work breakdown structure the project manager will have the ease of organizing and identifying key work streams that are required to be tracked and reported in the project which is currently undergoing.
Regularly Reviewing the Health of the Project
It is essential for all organisations that are undergoing some type of transformation, transition or delivering a project to check the health of the project on a daily basis. This is mainly because the project is currently under work-process and if there is a slight decrement in the health of the project then that can be amended accordingly and in due time before the projects depletes or collapse.
Establishing Clear Roles
It is essential to define all the roles and responsibilities of the whole project at an early stage, this is mainly because it is not a box-ticking exercise and should be inclusive of everyone involved in the whole project. This will hold everyone accountable and will allow everyone to know what is expected of them.
Reference List
Braun, V. and Clarke, V., 2012. Thematic analysis. American Psychological Association.
Clarke, V., Braun, V. and Hayfield, N., 2015. Thematic analysis. Qualitative psychology: A practical guide to research methods, 222(2015), p.248.
Gholami, B. and Murugesan, S., 2011. Global IT project management using Web
2.0. International Journal of Information Technology Project Management (IJITPM), 2(3), pp.30-52.
Guest, G., MacQueen, K.M. and Namey, E.E., 2011. Applied thematic analysis. sage publications.
Harris, H., 2001. Content analysis of secondary data: A study of courage in managerial decision making. Journal of Business Ethics, 34(3), pp.191-208.
Joffe, H., 2012. Thematic analysis. Qualitative research methods in mental health and psychotherapy, 1, pp.210-223.
Johhson, E. and Sylvia, M.L., 2018. Secondary data collection. Critical Analytics and Data Management for the DNP, p.61.
Marchewka, J.T., 2016. Information technology project management: Providing measurable organizational value. John Wiley & Sons.
Meredith, J.R., Shafer, S.M. and Mantel Jr, S.J., 2017. Project management: a strategic managerial approach. John Wiley & Sons.
Neuendorf, K.A., 2018. Content analysis and thematic analysis. In Advanced research methods for applied psychology (pp. 211-223). Routledge.
Schwalbe, K., 2015. Information technology project management. Cengage Learning.
Stewart, J.S., 2010. The role of the project management office on information technology project success. Capella University.
Tripathy, J.P., 2013. Secondary data analysis: Ethical issues and challenges. Iranian journal of public health, 42(12), p.1478.
Vartanian, T.P., 2010. Secondary data analysis. Oxford University Press.